BUUCTF 每日打卡 2021-9-5
## 引言
假期的最后一天(其实已经是到学校的第二天了),明天就要开始上课了 今天打了打 GrabCON CTF2021
[GrabCON CTF2021]Warm-up
 题目附件如下:
题目附件如下: 1
S01ZRENXU1NJVkhGUVZKUkpaRkZNMlNLSTVKVENWU0xLVlZYQVlLVElaTkVVVlRNS0pIRkc2U1dKVkpHV01LWEtaQ1VVVENXTlJORlNVS1dOUkdGS01EVUs1S0dXVlNLS1pDWFFUQ1ROUllFT1VUTE1STFZDTUxFSk5MR1c0Q0lLWVlEQ1RDWEtWMkZNVjJWTkJKRk1SS09MQktHV05EWktKV0U0VlNOTlJTRVdWVEtLSkxWR01CUklOTEdXNUNQS05XRkVSQ1dLWkhFSVVaUk9CTUZFMjJXS1ZKVENXU0tLWlZWVVJTVUdGTEZLVkNGR0ZIVTRSU1ZQRkdXWVRTTUtOVlRLVEtTR0ZSVEFVSlFNUkdGSVZUTUs1SkZNVExaS1pWWElWMk5OTkxFNFZUS0pKTFZJUkxRSlZKR1dNS1RLTVlEU1RDVk5OMkVRVjJXSlpLRk1WTFVKTkpUQ1VTRUtaV0U0VjJTR0JORklVU1dNUkxGTVJMVUpSSldXNkNYS0lZVlVSQ1RHQVlVT1ZDRk1STUU0VktPS0ZKVENTU0VLWldGTVZLUkdGU0U2VkxMTVJNVktNS1dNRktXV09LREtFWUZVVUNWTk4yRVFVWlJPQkdGTVJLT0s1S1RBM0NNS0pWWFFTQ1hLWlNFSVZMTE1SRFZJMjIySlJMR1dUU0hLSVlWVVMyV05OU0ZHVTMySkpGRksyM0VLVklWTVVTVUtSS1hJVDJXR0JORk1WTDJKSk1GRU1DMktOTEVLUlNXS05XRU1VQ1JOTlNFT1ZEMkpGNUZPVkxMR0ZKVEFXU09LWVlVNFJTVEdGWUVJVlJRTlJKRTIyWlZKNUtHV05LR0tWTEZVVkNXTk00VUdVM0xMSkZGSzIzWUtKSldXU1NMS0lZV0dNS1JHRkpFWVZMTEpaTVZLVlNPSlJLVEE1Q1NLNUtWRVZDV0tWSEZNVVJRSVVZRk0yMkdLWkpXVVZTSktaS0RBT0tRS1FZRFNVQ1JIVTZRPT09PQ==
 联系题面,不难猜想解密结果为base32加密密文,又找了一个base32在线解密工具,解密结果如下:
联系题面,不难猜想解密结果为base32加密密文,又找了一个base32在线解密工具,解密结果如下:  容易发现,解密结果又是base64密文形式,接着连续base64和base32解密,得到结果:
容易发现,解密结果又是base64密文形式,接着连续base64和base32解密,得到结果: 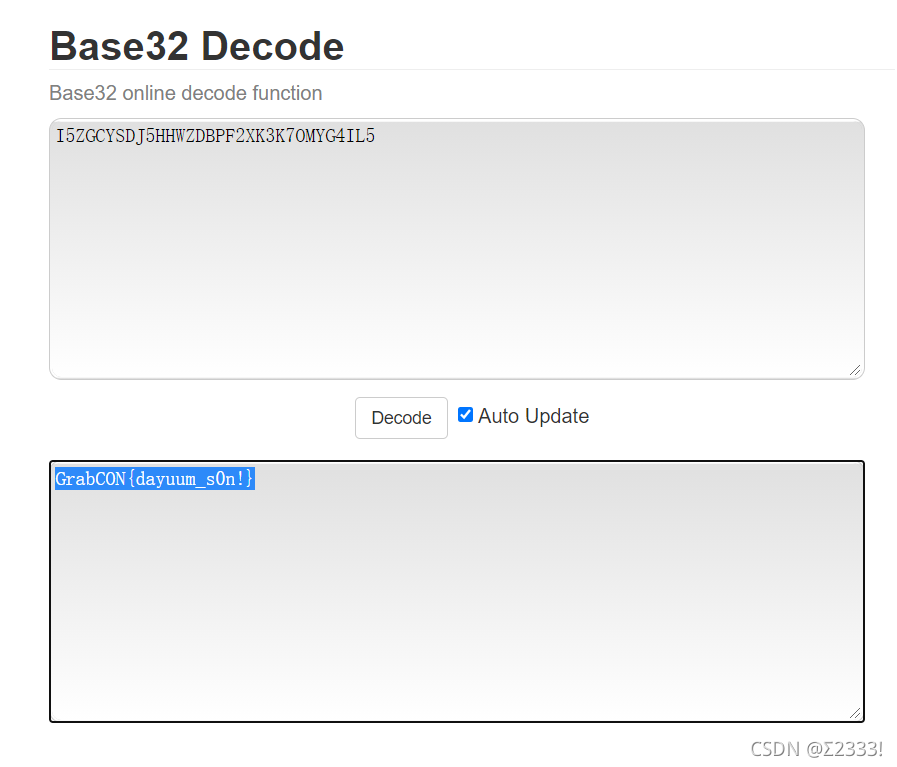
[GrabCON CTF2021]Poke Ball RSA
 附件内容如下:
附件内容如下: 1
2
3n = 498934084350094415783044823223130007435556803301613073259727203199325937230080661117917023582579699673759861892703348357714077684549303787581429366922208568924252052118455313229534699860304480039147103608782140303489222166267907007839021544433148286217133494762766492655602977085105487216032806292874190551319
e = 134901827939710543990222584187396847806193644190423846456160711527109836908087675183249532946675670587286594441908191054495871501233678465783530503352727362726294270065122447852357566161748618195216611965946646411519602447104878893524856862722902833460104389620397589021732407447981724307130484482495521398799
c = 100132888193232309251839777842498074992587507373917163874335385921940537055226546911990198769720313749286675018486390873216490470403470144298153410686092752282228631590006943913867497072931343354481759219425807850047083814816718302223434388744485547550941814186146959750515114700335721173624212499886218608818
1 | import gmpy2 |
得到结果如下: 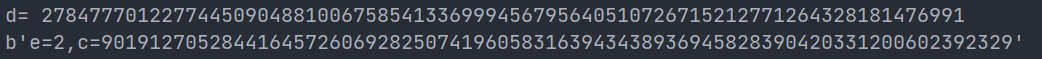 得到e=2,原本以为是rabin 但是分解n发现:
得到e=2,原本以为是rabin 但是分解n发现:  p,q都比c大,所以\(c^2 << pq=n\),直接开根就行,结果为:
p,q都比c大,所以\(c^2 << pq=n\),直接开根就行,结果为: 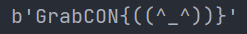
[GrabCON CTF2021]Old Monk's Password
 加密代码如下:
加密代码如下:
1 | enc = b'\x0cYUV\x02\x13\x16\x1a\x01\x04\x05C\x00\twcx|z(((%.)=K%(>' |
按照加密代码,密文的第一位即为随机数i,然后按照加密代码逐位异或运算即可,解密代码为: 1
2
3
4
5
6
7
8
9
10
11
12
13enc = b'\x0cYUV\x02\x13\x16\x1a\x01\x04\x05C\x00\twcx|z(((%.)=K%(>'
enc1 = b'\x0bPPS\r\x0b\x02\x0f\x12\r\x03_G\t\x08yb}v+--*+*8=W,>'
enc2 = b'\x07A[\x06\\\r\x15\t\x04\x07\x18VG]U]@\x02\x08&9&%\' 41".;'
def decode(cipher):
x = "hjlgyjgyj10hadanvbwdmkw00OUONBADANKHM;IMMBMZCNihaillm"
i = cipher[0]
m = ''
for c in cipher[1:]:
m += chr(c ^ ord(x[i]))
i = (i + 1) % 79
return m
print(decode(enc) + decode(enc1) + decode(enc2))
print('GrabCON{' + decode(enc) + '}')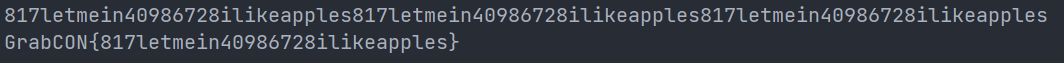
结语
可能要摸一段时间 希望继续坚持